The term “doppelganger” refers to a ghostly copy of a living person, down to their habits. In urban legend, seeing one in real life is believed to be a sign of misfortune or, worse, one’s imminent demise. If we go by William Wilson, a short story published by Edgar Allan Poe in the mid-1800s, it may be a bit of both.
Since it’s October, I might as well start things spooky.
But while the doppelganger may as well not be real, having an eerie lookalike certainly is. At the height of its disastrous data breach in 2017, Equifax established a website to assist those affected by the breach. The problem was that security expert Nick Sweeting managed to produce an almost one-for-one duplicate in less than 20 minutes.

Source: The New York Times
Apart from the content, the biggest difference was the URL. Equifax’s website on the left is equifaxsecurity2017.com, while the fake site on the right is securityequifax2017.com. The latter was so convincing that the company cited it multiple times, especially on their then-Twitter posts, before realizing the mistake.
Sweeting told The New York Times that he made the site to demonstrate how easy it was to impersonate it. If it were a person not as well-intentioned as him, it could’ve made things a lot worse for the credit reporting giant.
Yet, masquerading as a legitimate website forms the heart of what the industry calls SEO poisoning. It doesn’t get as much attention in the cybersecurity space, but it’s definitely a thing. Here’s everything you need to know about this black-hat practice.
No, wait, calling it black-hat is an understatement.
Good SEO for a Bad Website
SEO poisoning is the act of promoting malicious websites to the top of search results, capitalising on users’ tendency to trust top-ranked results. These sites are “doppelgangers” or duplicates of legit ones, down to the assets.
Only the URL differs, as no two websites can share the same domain name. Hackers are aware of this and use various workarounds, such as:
Typosquatting: Use a misspelled version of the target site’s domain name, hoping that visitors don’t notice the discrepancy. For example, a fake NOBS Marketplace site may have a domain name such as no-bsmarketplace.com or n0bsmarketplace.com.
Hijacking: Insert malicious links in parts of the target site, taking advantage of the fact that users usually don’t check the links before clicking. This is dangerous, as cybercriminals can execute this rather discreetly.
Fake Listings: Create fraudulent business listings that are identical to those of the target business and carry a link to the fake site. This becomes more dangerous if the company’s customers rely on local search.
Recently, hackers have turned to malware to perform SEO poisoning. Last March, Palo Alto Networks reported one such campaign in which Chinese-speaking threat actors developed a malicious version of an Internet Information Service (IIS) module called BadIIS. (1)
According to Unit 42, Palo Alto Networks’ threat intelligence team, BadIIS operates in two phases. The first poisons the target site with malware, which search engine crawlers then index in search results. The second involves waiting for an unsuspecting user to be led to the malicious site, known as a redirection trap. (1)
SEO poisoning is also employed in conjunction with outdated SEO practices, such as keyword stuffing and link farming. However, algorithm updates and awareness of modern SEO best practices have made this approach less popular.
Although still a minority compared to other methods, such as phishing, SEO poisoning is on the rise. Of the 700 cases Unit 42 has responded to between May 2024 and May 2025, around 12% involved SEO poisoning or malicious advertising (malvertising). (2)
Its Place in AI-Driven Search
“Wait a minute,” you might wonder. “Isn’t rankings-based SEO on its way out because of AI summaries? Doesn’t that mean SEO poisoning would eventually be pointless?”
If that’s how you think, then you clearly don’t know how cybercriminals operate. Take away one thing in hopes of stopping them, and they’ll find another way. In fact, many of them still rely on old-school tricks, like brute-force attacks, as many people still use weak passwords on their accounts. Other tricks don’t even need advanced hacker tech to be effective.
More importantly, recent studies have made it clear that rankings-based SEO may be more relevant than we thought. BrightEdge tracked overlaps between traditional Google rankings and AI Overviews over 16 months and found that overlaps were going up, not down.
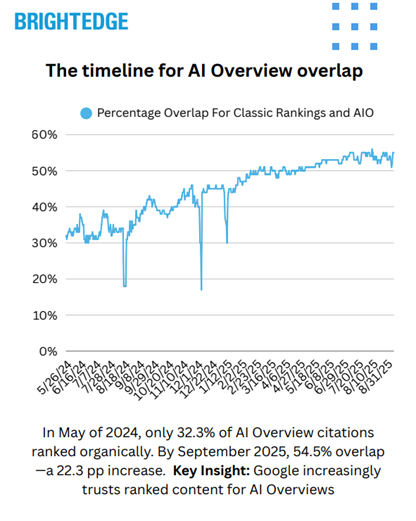
Source: BrightEdge
BrightEdge noted that the overlap rate varies wildly by industry. Most of the industries in the study registered an increase year-over-year, but the biggest winners were those that deliver Your Money, Your Life (YMYL) content. Among these were healthcare, education, insurance, and business-to-business (B2B) technology.
Now, it gets weird from here. When SEMrush conducted a study on the impact of AI-driven search on large language models (LLMs), it found that LLMs cited results in ranks 21 and below nearly 90% of the time.
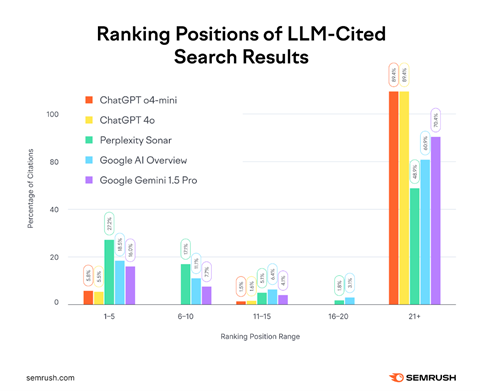
Source: SEMrush
It’s still unclear why LLMs behave this way, but SEMrush believes it’s built into their algorithm. Unlike conventional SEO, which considers a wide range of factors from on-page to technical, LLMs are more focused on drawing information. ChatGPT and Perplexity prioritise retrieving information over page experience.
If I were a hacker skilled at SEO poisoning (which I’m not), I’d see this as an absolute win. It means I can hide my malware in quality content and wait for AI tools to retrieve it. As some users may verify the accuracy of the AI summary before believing it, they’ll likely visit the cited websites one by one. The malware will then do its thing.
And the best part is that I don’t even have to try as hard to make my content rank at the top. I’d still try, though, because I’d prey on users’ trust in AI summaries.
By the way, this isn’t hypothetical. Cybersecurity experts refer to this tactic as an indirect prompt injection, which leverages an LLM’s retrieval process to help hackers slip their malware in. Assuming an LLM gathers up to 20 sources per query, manipulating two or three of them is enough for SEO poisoning to work its magic. (3)
Defending Against the Doppelganger
When left unchecked, a fake webpage or a compromised real one can deal serious, if not irreparable, damage to your brand as a whole. And I know you hardly have the patience or the resources to deal with an angry mob demanding something you didn’t even promise.
In 2023, a Connecticut car dealership was alarmed to receive calls from irate buyers who had been promised excavators or loaders from the same dealership. An investigation by the Better Business Bureau (BBB) revealed that it had been a victim of a website clone. (4)
As reported by the Connecticut Post, the dealership was deindexed from Google search results for one year and was unable to make online sales for a year and a half. The owner even contemplated shutting down the business, but the dealership is active to this day. (4)
SEO poisoning isn’t something you can solve with a good antimalware program, at least not on its own. As we’ve just established, the attempt can happen within and outside of your website. As such, your threat response has to cover both.
Enable HTTPS on Your Website
To begin, access your website and examine the part of the address bar.
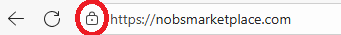
If that shows anything other than a padlock (or it says “Not Secure”), it means that your website isn’t running on Hyper Text Transfer Protocol Secure (HTTPS). It’s an indication that the connection between the browser and the website isn’t secure. I won’t get into the nuts and bolts here, but you can check out this guide by Cloudflare.
HTTPS should be the default for new websites, not just because it’s more secure than its predecessor. Some browsers, such as Chrome and Edge are designed to alert users if the website they’re trying to open isn’t using HTTPS. This can discourage users from proceeding, resulting in your brand missing out on valuable leads.
Also, not enabling HTTPS doesn’t even make sense from an SEO perspective. While not as weighty as content quality and links, HTTPS is still one of the few ranking factors confirmed by Google. You’d want your website to be compliant in as many aspects as possible to give it the best chance of ranking at the top. (5)
A word of caution, though. This tip alone won’t stop SEO poisoning, as cybercriminals can produce HTTPS-enabled websites of their own. That said, it can make specific techniques, like hijacking a bit more challenging.
Look Out for Traffic Spikes and Drops
Not all that glitters is gold. An uptick in traffic may seem like a good thing, but it can also signify a cyberattack—and it isn’t always a DDoS attack. Meanwhile, a sudden dip might indicate that the attack has already happened.
Use a website analytics tool (e.g., Google Analytics, Kissmetrics) to monitor unusual traffic spikes and drops. SEO poisoning involves redirecting traffic away from the real site to the fake one, and erratic movements of your line graph can indicate this.
Your analytics tool should be able to identify the source of traffic spikes. A small business serving a small community in the U.S. has no business generating traffic from, say, Europe or Asia. In fact, remember the Connecticut car dealership from earlier? The BBB’s investigation concluded that the source came from off the coast of Africa.
On the other hand, traffic drops are more challenging to manage. The first step involves ruling out reasons other than SEO poisoning, like a Google update or the search engine “absorbing” your traffic. SEO analytics tools, such as Ahrefs, can help with this.
Notify Key Parties, Especially Customers, ASAP
Whether a discovery or an attack occurs first, it’s essential to inform the necessary people. They include, but aren’t limited to, stakeholders (if any), your website hosting service, the appropriate government agencies, and especially your customers.
In reporting about the compromise, the U.S. Federal Trade Commission (FTC) suggests including the following pieces of information (may vary depending on your state’s laws): (6)
The specifics of the cybercrime
The information potentially stolen
How perpetrators used the stolen information (if you know)
Actions taken to resolve the matter
Actions taken to protect your customers’ information
Contact details of contacts in your business or institution
Consider releasing a separate statement to the general public on how to avoid falling into your doppelganger’s trap. It won’t be easy spotting red flags in a web design that’s one-for-one identical to yours, so always urge caution.
Don’t wait until you’ve resolved the issue to inform everyone. The longer you hesitate, the more data hackers can get away with. This is especially the case in SEO poisoning, as more uninformed visitors may make the same mistakes as the victims did.
Foster a Cybersecurity-Friendly Culture
Lastly, prevent your employees from falling into the trap by promoting awareness in the workplace. Teach them how to identify fraudulent sites and prevent their credentials from falling into the hands of unscrupulous individuals. In the event of a breach or suspicious activity, educate them on how to report it to the relevant authorities immediately.
Cybercriminals will resort to old-fashioned deception if given the chance, as it makes things easier and less costly. That’s the idea behind social engineering: forcing the victim into making a mistake that leads to them revealing their information. As such, there’s no such thing as being too careful in cybersecurity.
A Scourge to Safe Browsing
There’s no way to be certain that your website has a clone until things start happening. In that case, you only have so much time to act before your doppelganger starts damaging your brand’s image. Assume that your website has one and take every precaution to help protect it from the inevitable mischief.
References
1. “Operation Rewrite: Chinese-Speaking Threat Actors Deploy BadIIS in a Wide Scale SEO Poisoning Campaign,” Source: https://unit42.paloaltonetworks.com/operation-rewrite-seo-poisoning-campaign/
2. “2025 Unit 42 Global Incident Response Report: Social Engineering Edition,” Source: https://unit42.paloaltonetworks.com/2025-unit-42-global-incident-response-report-social-engineering-edition/
3. “How Threat Actors Are Rizzing Up Your AI for Profit,” Source: https://www.recordedfuture.com/blog/how-threat-actors-are-rizzing-up-your-ai-for-profit
4. “Bogus websites impersonated CT businesses to scam customers, BBB says,” Source: https://www.ctpost.com/connecticut/article/fake-business-scam-bbb-alert-20203864.php?utm_source=chatgpt.com
5. “HTTPS as a ranking signal,” Source: https://developers.google.com/search/blog/2014/08/https-as-ranking-signal
6. “Data Breach Response: A Guide for Business,” Source:https://www.ftc.gov/business-guidance/resources/data-breach-response-guide-business
